EY continues to grow its capabilities, talent pool and expertise in the security consulting services space. The cybersecurity practice is organised around five cybersecurity solutions, with Cybersecurity Transformation generating the most revenue for EY, and Cyber Operations as the fastest-growing solution. In the last year, Cyber Operations contributed 26% of cybersecurity revenue. EY’s cybersecurity service demand is increasingly delivered through a managed services engagement model. Additionally, the Americas continue to be EY’s largest area in revenue, while EMEIA experienced revenue growth, thanks to an acute shortage of cybersecurity talent leading to increased demand for managed services contracts.
Delivering security for transformation and managed services engagements
In a series of discussions since the start of 2023, TBR has spoken with EY’s global cybersecurity practice leaders to better understand how the firm continues to grow its capabilities, offerings, talent pool and expertise in the security consulting services space.
To set the stage, EY organizes around five cybersecurity solutions, including Cybersecurity Transformation, Data Privacy, Cyber Operations, Cyber Incident Resilience and Response, and the emerging Cyber for Assurance. Of the five, the first generates the most revenue for EY, in line with the firm’s traditional strengths around consulting, tax and strategy. Cyber Operations, which EY increasingly delivers through a managed services engagement model, has been the firm’s fastest-growing solution over the last year, contributing 26% of cybersecurity revenue in 2022.
Geographically, EY leaders said the Americas continues to be their largest area in terms of revenue, with clients across a full range of industries. In EMEIA, an exceptionally strong track record of revenue growth has belied an acute shortage of cybersecurity talent, leading to increased demand for managed services contracts as clients looked to EY to complete essential cybersecurity tasks.
In TBR’s view, EY continues to operate through a global effort, complicated by regulatory and compliance requirements that vary by country as well as member firms’ different partnership structures. However, at multiple times during the discussion, EY leaders said the firm knew that cybersecurity services required being “local to be there with clients.”
Expanding on managed services, EY’s Krishna Balakrishnan, Global & Asia-Pacific Region Cybersecurity Managed Service (CMS) Leader, noted that clients engaging the firm’s managed security services offerings increasingly look for platform-based approaches that will provide outcomes faster than previous expectations. As a result, EY more readily leverages emerging technologies to elevate the value of the firm’s managed security services offerings, supported globally by more than 4,000 cyber managed services professionals and nine cybersecurity delivery centers.
As consulting engagements typically lead to interest in managed services, TBR followed up with questions about how often clients seek stand-alone security services from EY, including managed services. Befitting a Big Four firm, EY leaders explained that they are “increasingly seeing an infusion strategy where cybersecurity also is infused into security-adjacent offerings such as tech/IT risk, regulatory and compliance management, as well ESG risk disclosures related to enterprise resilience such as requesting security parameters and maturity assessment of their cyber and CISO [chief information security officer] function as part of ongoing client engagements.”
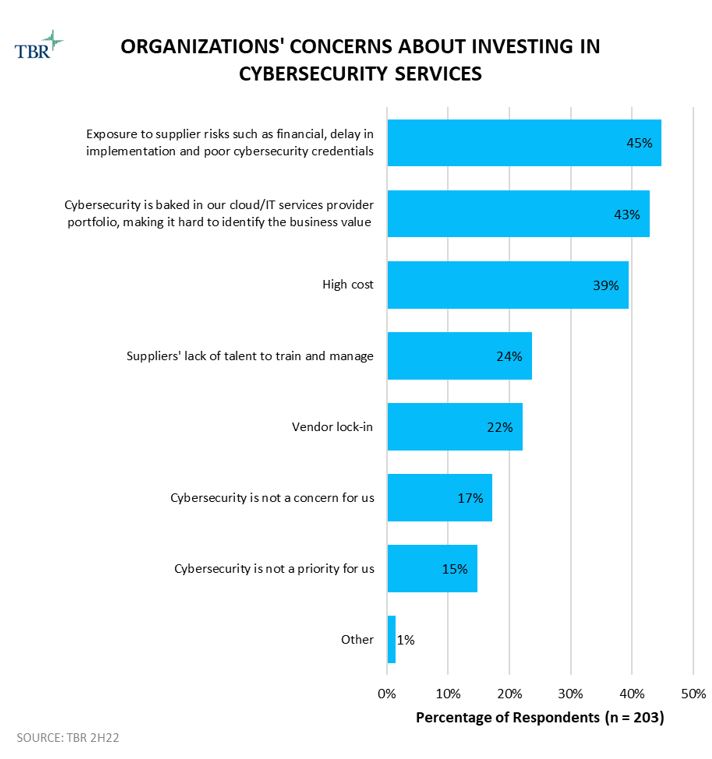
In TBR’s March 2023 Digital Transformation: Cross-Vendor Analysis report, we noted that, as shown above, “almost half of respondents ranked exposure to supplier’s risk as their organization’s top concern about investing in cybersecurity services, which puts pressure on vendors to develop properly scoped solutions and skilled and certified bench to gain buyers’ trust. Additionally, folding cybersecurity within vendors’ cloud and IT portfolio can be a double-edged sword if vendors do not build the use case and generate awareness around a particular cybersecurity capability area. This investment concern closely aligns with vendors’ ability to distinguish themselves as a leader in the space. Once again, the ecosystem is valuable, helping vendors to develop portfolio offerings aligned to their core value proposition and build a name for themselves, rather than just adding cyber on top of everything else they offer.”
Leveraging the ecosystem and being the best possible partner
During the discussion, multiple EY leaders stressed that the firm would not position itself as a technology company but would instead remain a consultancy aligned with technology companies to create transformative solutions — and not simply point solutions, but innovative and transformative solutions, cocreated with technology partners.
Expanding on this in follow-up discussions, EY Global Consulting Cyber Architecture, Engineering and Emerging Technology Leader Piotr Ciepiela described collaborations with Microsoft (Nasdaq: MSFT) and IBM (NYSE: IBM), Tanium and CrowdStrike, to name a few, and EY has launched several quantum security centers of excellence, complementing the IoT/OT Security Lab that EY opened in Warsaw, Poland, in 2018.
TBR asked how the lab had evolved in the last five years, and EY leaders explained that the firm uses it to “test customer deployments and conduct PoC [proof of concept] projects” as well as “show visiting customers a wide variety of cybersecurity solutions using the physical OT environment.” Ciepiela added, “At first, our EY clients wanted to test very specific OT solutions that were usually provided by startups and scale-ups. Today we are providing design and proof of concept for comprehensive OT environments dedicated to each OT sector.
With dozens of dedicated OT solutions as well as more than 350 physical and virtual environments, we can deploy and test entire ecosystems in days. That’s why [the] majority of our clients are coming back or treat our facility like lab ‘as a Service’ for new solutions and massive rollouts.” Circling back to technology partnerships, EY leaders described alliances and joint investments in physical centers dedicated to specific technologies, such as quantum and AI, with vendors as diverse as Red Hat, BT and Toshiba, in addition to EY’s strategic partners like Microsoft and IBM.
In TBR’s view, EY’s sustained emphasis on partnering well across the technology ecosystem — to include innovation, go-to-market initiatives, and even cobranded transformation centers, such as the EY wavespace innovation hub — has contributed significantly to the firm’s sustained success. TBR’s Voice of the Customer research confirms that clients prefer cooperative partnerships across an ecosystem of providers over a single vendor promising end-to-end solutions.
Further, regarding EY’s position within the larger security services ecosystem, EY leaders stressed that the firm does not pursue engagements based on requests for proposals or lowest-priced competitive bids; instead, it focuses on transformational work that leads to longer-term operations engagements. In addition, EY sees its greatest growth opportunities with clients in the financial services (although at a slower growth rate than previous years), energy, industrial/manufacturing, and public sector and defense sectors.
Simultaneously, EY leaders noted that Sectoral Security Operations Centers (SOCs) would likely become a significant trend across the cybersecurity industry, with EY intending to invest in SOCs that are dedicated to working with federal government, telecommunications and automotive clients, guided in part by client demand, as well as market research by EY-Parthenon and EY’s technology alliance partners. TBR has observed many IT services vendors and management consultancies develop strategies intended to focus on a select number of industries, with unsatisfactory results or abandoned strategies often tied to simply trying to focus on too many sectors at once. EY’s clear delineation around Sectoral SOCs looks to be a more tightly defined strategy, playing to the firm’s strengths and the market opportunity.
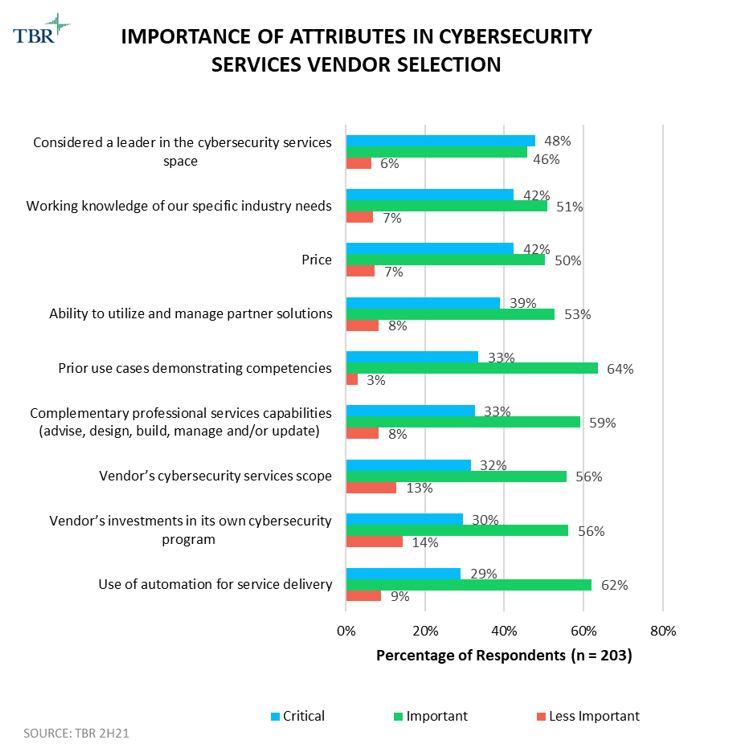
In the upcoming March 2023 Digital Transformation: Cross-Vendor Analysis report, TBR notes, “Almost half of survey respondents consider vendors’ brand leadership position to be a critical attribute for cybersecurity services. We believe this is a hard balance for vendors to strike, especially as cybersecurity can often be an unheralded area, so touting strength through use cases and/or portfolio offerings can entice malicious actors to exploit weak areas. Industry knowledge and price ranked as the No. 2 and No. 3 critical attributes, respectively, which is not surprising given the need for demonstrating regulatory and compliance knowledge tied to industry specialization during macroeconomic downturns. The No. 4 most critical attribute is vendors’ ability to rely on their partner ecosystems, which can be a challenge in the world of security as vendors try to protect their IP and best practices.
“We see partnerships between management consultancies and cyber-specialized vendors to be best aligned here as the former can bring in the risk and compliance knowledge and the latter group remains responsible for developing and managing the tech stack. While using automation for service delivery ranked the lowest in terms of being a critical attribute, we believe vendors need to consider elevating the value of automation as a tool that supports updated business continuity plans, especially as it allows them to address price-conscious buyers.”
What sets EY apart: Being EY
Three characteristics of EY’s cybersecurity practice stand out to TBR as key to the firm’s success to date and smartly playing to its strengths going forward: offering a whole-firm approach and delivery; partnering well across the ecosystem; and being simultaneously global and local. Throughout discussions with TBR, EY’s global cybersecurity leaders stressed that security services are complementary to the firm’s full range of services, including tax, risk and consulting; security is part of the package, not a stand-alone offering.
In TBR’s view, that approach builds on EY’s long-established brand as a trusted partner that is well versed in a client’s financials, operations and strategies, while also echoing a common refrain from clients themselves: security must be baked into everything. Most of EY’s peers also espouse a whole-firm approach to services, including cybersecurity, making this a necessary characteristic, rather than a differentiating one, that reinforces one of EY’s strengths.
The cybersecurity ecosystem may be the most diverse within the larger technology space, with seemingly endless pure play firms and every IT services vendor and management consultancy providing security services. In that maelstrom, EY has demonstrated a willingness and ability to play well, enhancing the technologies and capabilities of strategic alliance partners and vetting, nurturing and accelerating the development of smaller firms without compromising EY’s core value proposition around trust and transformation.
In an email exchange earlier this month, EY answered TBR’s questions about whether the firm will expand partner-branded SOCs by noting, “We already have several partner-aligned SOCs developed in partnership (U.S./EMEIA mainly) with our Big Six Alliance Partners, i.e., SAP [NYSE: SAP], Microsoft, ServiceNow [NYSE: NOW], IBM, Adobe [Nasdaq: ADBE], and now Dell Technologies [NYSE: DELL], and will continue to expand our partner-cocreation facilities and IP at pace.”
As with the whole-firm approach, EY’s alliance strategy does not provide, on the surface, easy differentiation from its Big Four peers, other management consultancies or most IT services vendors. TBR does believe EY’s difference may come through the breadth of these partnerships, EY’s willingness to cobrand SOCs, and the firm’s insistence that it stay within its only lane — which, as noted above, is not as a technology company but as a consultancy aligned with technology partners that can help deliver trusted transformation, including in the security space.
Lastly, EY’s global cybersecurity practice recognizes that every client’s security needs remain highly localized, even if the client maintains global operations. People, always the biggest security risk, physically reside somewhere. Regulations and reporting mandates start at the national, or sometimes state and local levels, requiring on-the-ground expertise and assurance. Any global cybersecurity services provider has to blend the need for borderless reach and capabilities with highly localized talent and expertise.
Once again, EY’s strengths and capabilities do not make it unique among peers, but a commitment to seamless and highest-quality security services at any client’s location, including the necessary talent on the ground lends credibility to EY’s claim that the firm is a market leader for cybersecurity. In TBR’s view, EY has nurtured three critical characteristics, playing to the firm’s strengths while positioning for growing opportunities in the cybersecurity space. In a crowded and noisy marketplace, EY seems to have found its place as a trusted, global, local, widely capable partner to technology partners and clients.
Our most-read analysis, free in your inbox each week — Subscribe today!



Nothing Found
Sorry, no posts matched your criteria