Built for this moment: Optiv evolved to full-stack security services
Expanded security services well beyond value-added reseller
On July 28, TBR attended a presentation and Q&A session held by Optiv’s leadership team, including CEO Kevin Lynch and SVP for Cyber Defense & Applied Security Jason Lewkowicz, who discussed the company’s overall strategy, place in the market and core cybersecurity offerings. They were later joined by a broader Optiv team for a deeper dive into some specific security services offerings. The following reflects that session as well as TBR’s ongoing research into and analysis of the cybersecurity services practices of leading IT services vendors, cloud vendors and software vendors.
For TBR, CEO Lynch captured Optiv’s essence when answering a question about change management by emphasizing how much Optiv itself has evolved and will continue to do so. Lynch said the company’s services business has changed significantly in the last couple of years. Previously, Optiv provided mostly attached technical services, bringing in third parties in a standard VAR business model. With expanded capabilities, Optiv expanded its footprint at clients and has shifted its focus to business outcomes, reflecting an evolution in how chief information security officers (CISOs) see their value in an organization. Lynch described Optiv as “the last mile in a tech ecosystem” and said his company was built for this particular moment in cybersecurity services, as Optiv combined “great technical acumen in the field,” proximity to clients, and technology ecosystem partnering done in “a unique way.”
In TBR’s view, Optiv unquestionably benefits from deep expertise in deploying and integrating a wide range of technologies across the security space and executing a business model pivot from VAR to a full range of consulting, integration and managed services capabilities. Private equity ownership and the ability to attract top security talent undoubtedly have helped the company expand. Sustained growth in the near to medium term will likely depend, in TBR’s view, on Optiv’s ability to scale current capabilities without compromising quality, expand brand recognition within the ecosystem as more than just a VAR, and deepen the company’s footprint with clients without overextending outside its core security services offerings.
Close to clients, and delivering on technology and services
Optiv’s presentation included details about the company’s current business, which has over 2,300 professionals serving approximately 6,000 clients, predominately in North America. Lynch noted that the company’s revenues expanded at a double-digit growth rate from 2020 to 2021 based on two growth pillars: technology, which includes reselling technologies and solutions from 450 partners; and, services, which includes a 650-plus-person team of experts with deep technical talent working directly in the field on clients’ specific business and security challenges, supported by larger delivery and Security Operations Centers teams.
Lynch said clients vary widely by revenue size, and most of Optiv’s talent works in close proximity to clients’ sites, with the company operating just three main hubs in Kansas City, Kan.; Denver; and Bangalore, India. For context, TBR notes that Atos has a little less than three times as many security services professionals generating around $750 million annually, Accenture Security (NYSE: ACN) claims a headcount almost seven times Optiv’s with revenues close to $6 billion, and Deloitte has close to 10 times the headcount of Optiv and revenues near $4 billion. Those figures likely include professionals in roles not specific to security who provide industry knowledge, consulting or systems integration in coordination with more specialized security services engagements, but the overall scale of those three vendors challenges Optiv in terms of talent and client mindshare.
Meeting clients where they are with advice, implementation and managed services
Shifting to a discussion of how Optiv provides security services to clients, Lynch described three “modalities”: advise, deploy and operate. In the first, Optiv views its clients as deserving of “great advice on what to do in this unprecedented time,” leading the company to provide security strategies, insights, design and envisioning of desired future operational states. The second modality, deploy, constitutes the shift from “thoughts to actions,” as described by Lynch, and includes an evaluation of which technology assets should be deployed, validation of a client’s existing technology, sourcing by Optiv of fit-for-purpose technology, and integration into a client’s environment.
After this stage, according to Lynch, some clients ask Optiv to become a full-on security partner, taking over the operations of the client’s security apparatus through a managed services arrangement. Lynch said these clients typically recognize that Optiv’s security expertise cannot be replicated in-house, in part because these clients’ core business value does not come from security while Optiv’s does. He added that Optiv “will build the product stack to deliver on this promise” of providing “the entirety of [some clients’] security needs,” but cautioned that because Optiv has “to be perfect when we deliver,” the company continues to build out these capabilities to meet their ambitions.
Diving further into Optiv’s approach, SVP Lewkowicz noted Optiv has shifted its focus to making its services simple for clients to consume, in part by meeting a client “wherever they are on the security journey.” In describing some of Optiv’s security services, Lewkowicz said the company’s Strategy and Governance practice works with clients lacking core competence and expertise around security, helping those clients set desired outcomes; the Digital Transformation practice examines the full spectrum of enterprise technology for security implications, too often after a client has already started a digital transformation journey; and the Risk Management practice helps clients measure risk through the right security and compliance lenses.
In describing these offerings, which Optiv includes under an overall Cyber Strategy & Risk practice, complemented by a Cyber Protection & Identity practice and a Cyber Defense & Applied Security practice, Lewkowicz acknowledged the role of Optiv’s 450 technology partners and said the company is the “connective tissue” between technology and services.
TBR noted throughout Lewkowicz’s presentation an emphasis on highly flexible scoping arrangements, with Optiv content to meet a client’s every security need or just a small set. In TBR’s experience, most security services vendors take a more proscriptive — or at least an encouraging with some pressure — approach, potentially leading clients to take on more than they are prepared for. Both Lewkowicz and Lynch stressed that Optiv’s overall culture engendered a flexible and client-centric approach, potentially providing a strength against other security services vendors.
One additional note on Optiv’s approach: Lynch described his company’s decision to work with 450 technology partners as a strategic choice, saying they could work with 3,000 or more players across the security technology spectrum but had narrowed its ecosystem down to 450 to make Optiv a “value-added convener of IP.” He said that all 450 technology partners engage in go-to-market motions with Optiv and that the company wraps services around some of those technology partners’ solutions.
For a select group, perhaps as few as seven partners among the 450, Optiv cocreates and builds integrated solutions. This pyramid of partners strikes TBR as refreshingly honest — no company could adequately manage 450 relationships to a uniform degree of commitment and investment. Many larger, multifaceted IT services providers have established services-plus-technology partnerships, often described as business groups, to advance go-to-market strategies with specific technology vendors, such as Amazon Web Services (Nasdaq: AMZN), Microsoft (Nasdaq: MSFT), Google (Nasdaq: GOOGL) and SAP (NYSE: SAP). While a seemingly successful strategy for IT services vendors, TBR does not believe that kind of branded approach, an explicit tie to a massive technology provider, would benefit Optiv.
As CISOs face uncertainty, Optiv provides focus, capabilities and experience
During his remarks, Lynch provided a passionate assessment of Optiv’s place in the market, noting that his company is “built for this moment, for this challenging time for our clients” and “we can stand shoulder to shoulder and help solve problems.” He added that Optiv’s heritage as a value-added reseller provided a solid foundation for evolution to a full-breadth security services company. “We don’t start and stop with [a VAR role],” he explained, “but bring consulting and tech talent to wrap around solutions and provide integrated outcomes.” Lynch contrasted Optiv with IT services vendors and consultancies that have a security services business as part of their overall suite of offerings and capabilities. Optiv just does security, and in Lynch’s telling, clients appreciate that singular focus.
Lynch spoke at length about the current challenges facing CISOs, including a challenging market for talent, accrued technical debt and legacy tools, many of which are not integrated and cannot coherently and consistently deliver business, data or technology outcomes. Added to this environment, Lynch said CISOs face changing reporting structures and must now do more than simply provision technology; CISOs now have to deliver business results, a shift Lynch described as “from inputs to outcomes.” Further, Lynch said cybersecurity attack surfaces and perimeters got stretched because of the pandemic and remote working, raising questions for CISOs about whether that expansion would become permanent. Lynch speculated most enterprises would remain hybrid for the coming decade, resulting in sustained demand for security services.
To meet these challenges, Lynch said Optiv brings its twin technology and services pillars, as well as the full 450-partner ecosystem, in a differentiated way, delivering full capabilities against CISOs’ current needs. In addition, the company launched its first solution using its own processes and will be aggressive in the near term on innovation and development, potentially also using acquisitions to expand across the market and into additional geographies.
Lynch and John Johnson, Optiv’s VP for Cyber Strategy & Transformation, noted competitors provide technology solutions but rarely have the ability to identify system dependencies and do not focus on business processes, leading to gaps in data and understanding about clients’ business-critical processes. Johnson noted that traditional IT services providers and consultancies do not approach resiliency and recovery with the same rigor as Optiv, speculating that these competitors perhaps lack talent who have responded to real and substantial ransomware attacks. On a final note about differentiation, Lynch said Optiv has experienced people who have seen the bad outcomes that can happen, are battle scarred and know what is really needed.
TBR has written extensively about IT services vendors’ and consultancies’ cybersecurity practices, having been briefed by those vendors, visited security operations centers and seen demonstrations of leading-edge solutions. But even with scale and people who are passionate about their craft, those security services practices remain only a part of the vendor’s or company’s overall business. Lynch is right in saying Optiv’s focus on only cybersecurity separates his company from competitors, no matter those competitors’ scale and client base.
Further, TBR’s research on digital transformation (DT) (see Figures 1, 2 and 3) illustrates two trends beneficial to Optiv: buyers continue to make security a priority, and buyers increasingly want an ecosystem of vendors, not “one throat to choke.” Optiv’s business model pivot to expanding beyond being a VAR, combined with the expertise Optiv has been recruiting in recent years and an emphasis on consulting — yes, Optiv now does change management consulting as part of its cybersecurity strategy engagements — appears to round out a complete picture of a most capable security services company that is well suited for the coming changes in the security services market. In Lynch’s words, TBR believes Optiv may be “built for this moment.”
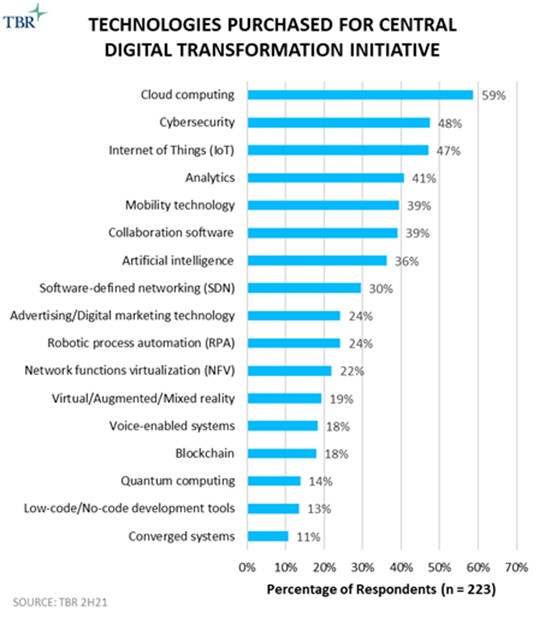
Figure 1
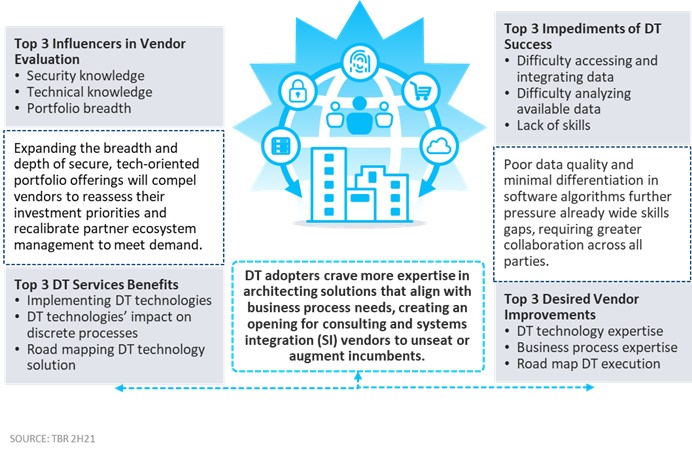
Figure 2
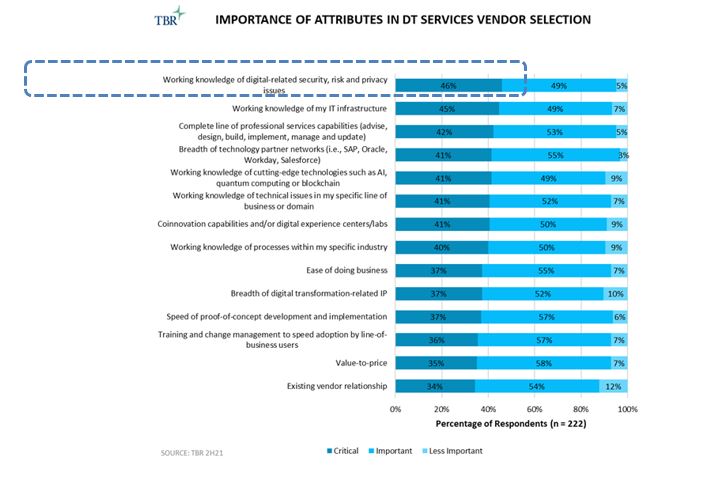
Figure 3
TBR includes coverage of cybersecurity services in individual vendor reports, benchmarks and market landscapes, with all analysis based on the individual strategies, performances and activities of the IT services vendors and consultancies in TBR’s scope. Foundational reports used for this special report include IT Services Vendor Benchmark, Digital Transformation Insights Report: Voice of the Customer Research and Management Consulting Benchmark. Access these reports and more with a 60-day free trial of TBR Insight Center™.




Leave a Reply
Want to join the discussion?Feel free to contribute!